
Technology has become an important part of our lives and to a great extent, we have come to depend absolutely on it. It affects all areas of our lives because of the solutions it proffers to the numerous challenges we experience. However, the trust hinged on technology is as much as looking at the green light and being confident that you can pass safely, that online debit and credits data are safe from unauthorized access, and that our smart devices cannot be compromised. It is estimated that around 2020 there will be about 30 billion devices linked to the Internet.
Unfortunately, there has been an increase in the trend of malicious attacks since devices have become more artificially intelligent and interconnected. This has obviously lead to numerous consequential privacy and security risks that later posed huge threats to the safety and security of internet users. Moreover, these breaches do not end at just the devices being compromised, but also, the important details of the users found on these devices and cloud-related services accessible to such compromised devices are also made vulnerable.
These compromised devices may contain typical important details of individuals that range from utility bills, medical bills, to banking information and private communication that involves family and friends. It is proven that when these sensitive data end up in the wrong hands, they end up being sold on the dark web or used for other malicious purposes which become very consequential to the owners of such information which could be a company, industry or government.

Globally, the level of insecurity and the actual cost of data breaches and cyber crimes are at an overwhelming high, where 72% of huge businesses recorded a cyber attack and almost half (47%) of the US firms encountered at least a couple or several cyber attacks. Additionally, about 3 billion personal information has been stolen and sold on the dark web. Virtually everybody who is connected to the Internet has experienced some form of data infringement.
Modern pertinent solutions have shown that they cannot keep up with the soaring increase in the number of intelligent cyber crimes and threats facing our systems every day. Unfortunately, the signature-based threats used to look out for new attacks are futile since there are new and not sighted threats previously. This is assuming that when the threat vector is recognized while the signatures are fully up to date, they are functional. Looking at the level of next-generation intelligent attacks; one can only conclude that these reactive solutions lack the poise to protect individuals.
As more technological advancements are being made in the areas of smart machines and systems like self-driving vehicles, smart cities, smart houses, medical implants and the likes, it is obvious that employing the present security measures will significantly expose these innovations to numerous vulnerabilities.
The available next-generation solutions available are solely built and kept by enterprises, large corporations and governments to provide solutions to various problems. This is done without the small to medium businesses and families in focus because they are quite expensive, making it inaccessible to the larger majority.
The available next-generation solutions available are solely built and kept by enterprises, large corporations and governments to provide solutions to various problems. This is done without the small to medium businesses and families in focus because they are quite expensive, making it inaccessible to the larger majority.
The Heroic cybersecurity project is an imperative innovation which is a decentralized, intelligent, and incentivized cybersecurity based on blockchain technology consisting of a three-fold core project. These projects are conjoined to protect against the prevailing modern and next-generation cyber threats while offering a functional security solution that is of assistance to basically all types of users which consists of the individual users, the developers, and the organizations. These projects include:
- Arc reactor
- Guardian
- Research and Development Environment
These systems result in an uncommon method of building a maintainable and sustainable ecosystem that is constantly evolving for cyber threat protection. When the Heroic ecosystem is fully functional it will provide the necessary resources to intelligently fight against the existing threats and the cyber threats of the next generation.

The Heroic arc reactor is a decentralized and open repository for cyber threats intelligence exchange. This repository is powered by the blockchain and it is intended to be an open depository with an easy programmatic access to the data, and an operative marketplace for the data.
The Arc reactor will be intelligent and the data deposited with its attributes are trained to be used after passing through an extraction process. The data obtained will be used to train machine learning algorithms which will definitely permit the scoring and classification of samples. As data providers and more individual users join the ecosystem, it is expected to become more robust and intelligent, offering more cybersecurity-related products.
The basic functions of the Arc reactor is to collect, transform, and distribute threat data.
The Guardian is a compact cloud-based cybersecurity platform that offers an easy online interface for individuals users, families and businesses to handle all pieces in the cybersecurity riddle. Guardian understands the threats data using the information gained from the Arc reactor and combines it with artificial intelligence to avert cyber attacks.
The Guardian will also assist software developers and organizations to build further integration to connect the Guardian with its data layer. This will also lead to the monetization of their creation, thereby giving the platform a more wholistic interface.
The R and D environment will offer individual users, company, and organizations a nerve center to get acquainted visually and programmatically of a record of threat data in real time provided by the arc reactor. This will offer the developers the opportunity to develop and test their own algorithms in a safe, hosted environment. Thus providing access to community-sourced algorithms and software to analyze and block threats while creating actionable artificial intelligence.
Heroic.com is loyal to furnishing the supply of the data, tools, and software required to create the future generation of AI-powered cybersecurity while facilitating and incentivizing open source software solutions as demanded.
Heroic.com has been designed to make available manifold levels of access while adding value and assistance in order to motivate an accelerated research enhancement and an integration of an advanced cybersecurity technology. This is asides guaranteeing a global access to these technologies making the Ecosystem to grow thus making it stronger.
Heroic.com is utilizing the Ethereum blockchain in the issuing of its native cryptocurrency HRO tokens. The HRO tokens will be used as a form of authorization, incentivizing users and developers, as a means of settlement. HRO tokens comply with the ERC-20 standard for transactions which expedites direct payment between the ecosystem users, organizations and software developers. A fixed number of HRO tokens will be issued.

The ICO pre-sale is underway and the price has been pegged at 1 HRO = $0.1125 USD.
More details on contribution details can be found at https://tokensale.heroic.com/ and https://tokensale.heroic.com/contribute/
More details on contribution details can be found at https://tokensale.heroic.com/ and https://tokensale.heroic.com/contribute/
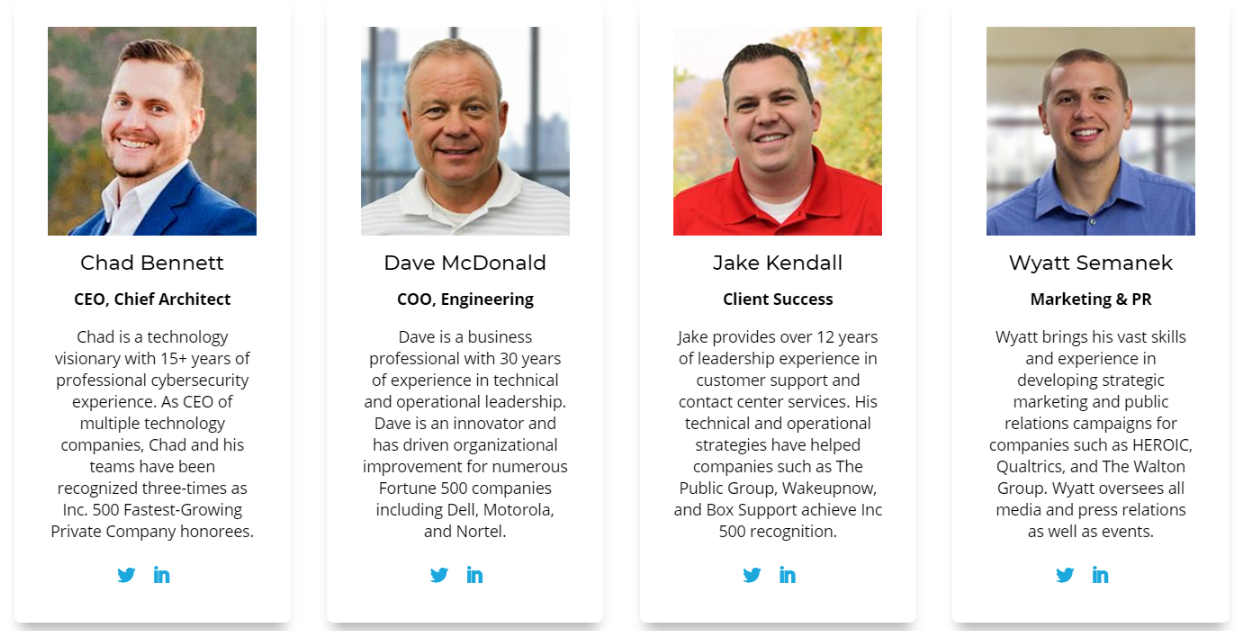
The brains and muscles behind the Heroic.com decentralized cybersecurity solution are noteworthy individuals in their various areas of expertise with a wealth of experience spanning decades, ranging from cybersecurity, operational leadership to software development and customer support.
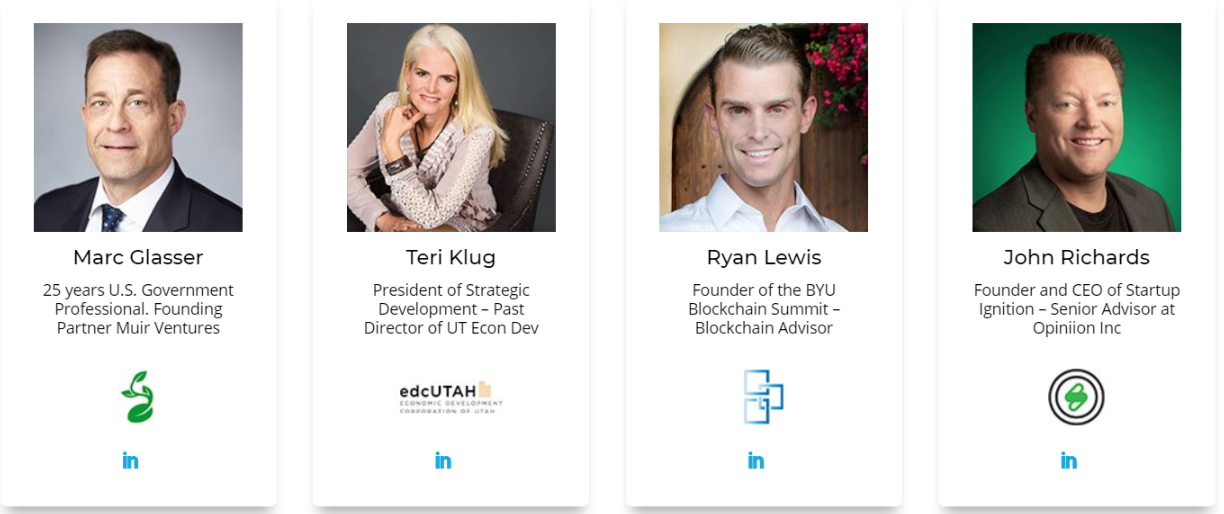
The advisors of the team are credible, high-profile individuals with not just influence but experience in various aspects of technology, some of whom are CEOs, entrepreneurs, and highly-placed individuals in various aspects of technology. A brief of their various profiles is given below:



Heroic.com has entered into a strategic partnership with top blue-chip companies and security firms in a bid to ensuring not just the further development but also, the security of the internet for the safety of the private data of internet users.

For more details about the project, use any of the links below:
WEBSITE: https://heroic.com/
WHITEPAPER:https://tokensale.heroic.com/wp-content/uploads/2018/02/HEROIC_White_Paper_V1.pdf
TELEGRAM: https://t.me/heroicdotcom
TWITTER: https://twitter.com/heroiccyber
FACEBOOK: https://www.facebook.com/heroiccybersecurity/
YOUTUBE: https://www.youtube.com/c/HEROICCybersecurity
MEDIUM: https://medium.com/heroic-com
WEBSITE: https://heroic.com/
WHITEPAPER:https://tokensale.heroic.com/wp-content/uploads/2018/02/HEROIC_White_Paper_V1.pdf
TELEGRAM: https://t.me/heroicdotcom
TWITTER: https://twitter.com/heroiccyber
FACEBOOK: https://www.facebook.com/heroiccybersecurity/
YOUTUBE: https://www.youtube.com/c/HEROICCybersecurity
MEDIUM: https://medium.com/heroic-com
0 coment: